By enabling the firewallD logging for a denied packet on the Linux operating system, where the firewallD will manage the Linux firewall dynamically in order to protect your network connections, interfaces and services.
This blog will explain How to enable the firewallD logging mechanism for denied packets on the Linux operating system. You can also take the help of our expert team to get it done on your behalf,more detail refers to our server management plan for further assistance.
First, need to set the logDenied options in the etc/firewalld.conf file/ firewalld. Once the enabling is done, then Linux will log all the packets that are rejected by the firewallD.
Methods to enable the firewallD logging.
firewalld.conf method
firewall-cmd method
firewall-config method
Configuring logging for denied packets {Firewalld.conf method}
First, you need to edit the /etc/firewalld/firewalld.conf
sudo vi /etc/firewalld/firewalld.conffind
LogDenied=off
Replace
LogDenied=all
Then save and close the file. Run the follow command and restart the firewallD service.
sudo systemctl restart firewalld. serviceBy default, the log denied option is turned off. Turn on the log denied option on logging rules right before the reject and drop rules in the INPUT, FORWARD, and OUTPUT chains for the default rules and also reject snd drop rules in the zones. Possible values are all, unicast, multicast and off.
Use the combination of the grep command and the sed command for the shell scripts.
grep '^LogDenied' /etc/firewalld/firewalld.conf
grep -q -i '^LogDenied=off' /etc/firewalld/firewalld.conf && echo "Change it" || echo "No need to change"
grep -q -i '^LogDenied=off' /etc/firewalld/firewalld.conf | sed -i'Backup' 's/LogDenied=off/LogDenied=all/' /etc/firewalld/firewalld.conf
Firewalld enable logging {firewall-cmd method}
Find and list the log denied settings
sudo firewall-cmd --get -log -deniedThen change the actual log denied settings
sudo firewall-cmd --set-log-denied=allVerify and run the following commands.
sudo firewall-cmd--get-log-denied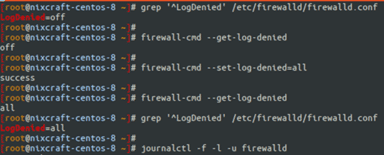
Enabling the firewalld log using the GUI configuration tool(firewall-config method)
Fedora or CentOS or openSUSE desktop users can try the GUI method. First, you need to open the terminal window and then open the firewalld GUI configuration tool. Run the command and start the firewall-config.
firewall-config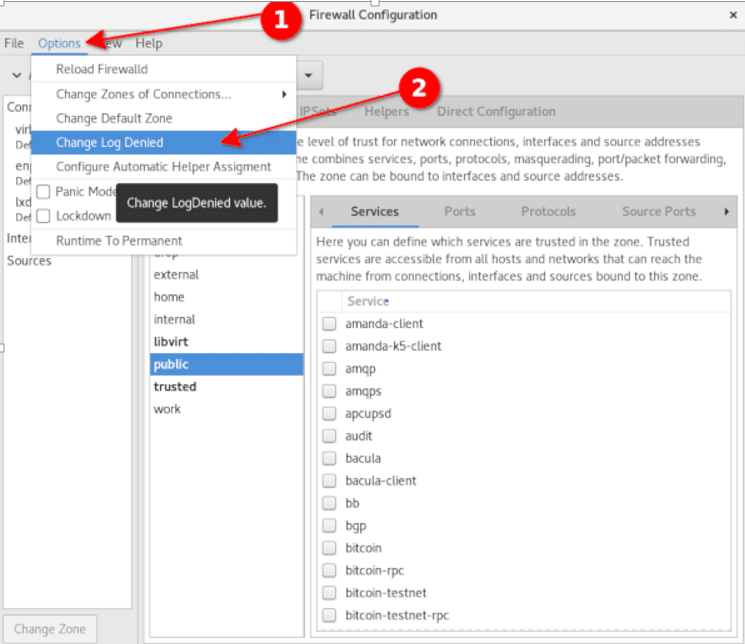
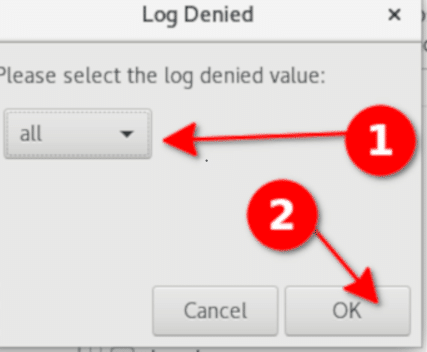
Choose and click the “option” menu and select the “change log denied”option. Choose the new LogDenied setting from the menu and click the “ok “button.
How to view the denied packets?
Run the following command to view the denied packets.
journalctl -x -e
Or use the combination of Dmesg and grep as follows:
dmesg
dmesg | grep -i REJECT
How to log all dropped packets to /var/log/firewalld-droppd.log file
First,create a new config file called /etc/rsyslog.d/firewalld-droppd.conf on the CentOS/RHEL v7/8 server.
$ sudo vim /etc/rsyslog.d/firewalld-droppd.conf
Then add the following configuration
:msg,contains,”_DROP” /var/log/firewalld-droppd.log
:msg,contains,”_REJECT” /var/log/firewalld-droppd.log
& stop
$ sudo systemctl restart rsyslog.service
Try to login by using the cat command/grep command/egrep command or tail command.
$ sudo tail -f /var/log/firewalld-droppd.log
Conclusion
It is an essential task for Linux administrators to keep an eye on the rejection and dropped packets by using the firewalld. It ensures security issue and avoids monitor attacks. So it is necessary to enable the log dropped packets using the firewalld in RHEL/CentOS/Fedora and SUSE/OpenSUSE Linux.