The internet is a hostile environment, together with the web hosting face innumerable threats through the bad actors that will steal the data and exploit server resources. Whereas CentOS is secure and a stable foundation that is not invulnerable. The malicious bots and the bad actors will access via software vulnerabilities, configuration mistakes, and poor Linux security practices.
If you need any assistance related to Linux server management services, please consult our technical team support for further detail information.
The Cpanel and WHM include many Linux security tools which help server administrators in order to build a secure hosting environment. Let’s have a peek at four techniques that leverage Cpanel and WHM that will enhance Linux security.
Hanging the SSH port to confuse bad bots.
Implementing SSH keys to avoid security vulnerabilities caused by weak passwords.
Automatically blocking brute-force attacks with cPHulk.
Leveraging cPanel Security Advisor to mitigate common Linux security problems.
Switch the SSH port in cPanel
The SSH (secure shell) is an encrypted network protocol that ensures the authentication credentials and the data safe while connecting to the server’s shell. The client on your local device connects to the server that runs an SSH service. Whereas communication between them is encrypted so that data will travel securely over the network.
The SSH service traditionally listens for connections on harbour 22, so bots can easily target the port with the brute-force attack that attempts to guess and access valid information such as username and the password. Try to choose a strong password so that it never allows brute force to access the port.
Before you proceed, ensure the change in your firewall to allow the connection on the fresh port. Otherwise, it will block the SSH connection and you will be unable to login into it.
Log in as root by using SSH and open typically the/etc/ssh/sshd_config file in the preferred text editor.
nano/etc/ssh/sshd_configFind the line that scan.
#port 22Delete the pound indicator at the beginning of the line and then change the 22 to your port.
port 32356Save and close the SSH configuration and finally restart the SSH service.
/script/restart_sshEnsure to note the port number. Whenever you log into the SSH need to specify the port in your ssh command.
ssh -p 32356 [email protected]Best way to use SSH keys with the root account.
By changing the SSH port will reduce the brute force attempt, but it will not stop motivated attackers. Another way to boost SSH security is to avoid the password in favor of SSH keys.SSH keys are more secure and, if it turns out password logins are disabled, they make successful brute-force attacks impossible.
The SSH points have a public and private component. Whereas the public key stored on the server and a private key stored on the client’s machine. Only the user with the private keys can be log into the relevant account.
First generating the new SSH keys for the root in WHM. For that, you need to login into the WHM and navigate to Manage root’s SSH keys.
Click Generate New Key.
Complete form with a robust password. In most situations, the default settings are fine.
Press Generate major
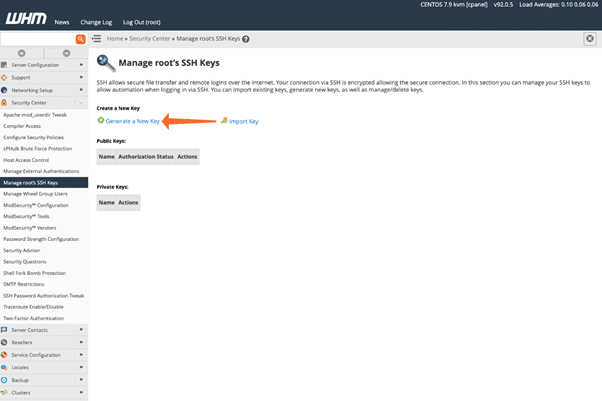
WHM generates the public keys and the private keys, you can see it by clicking Return to help SSH manager. Next, authorize the public key element for authentication. Select the manage Authorization and then click the Authorize.
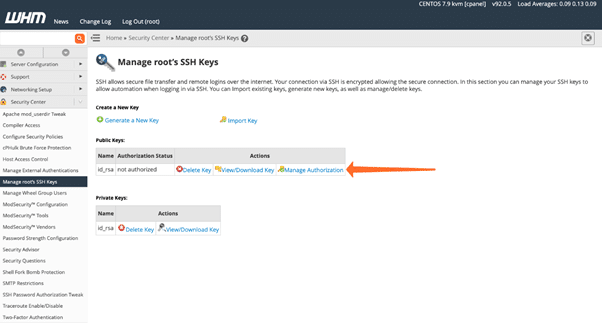
Download and save the private key on your local computer. Click view/download key. Copy the text from the upper text box and then use the putty client on the windows.
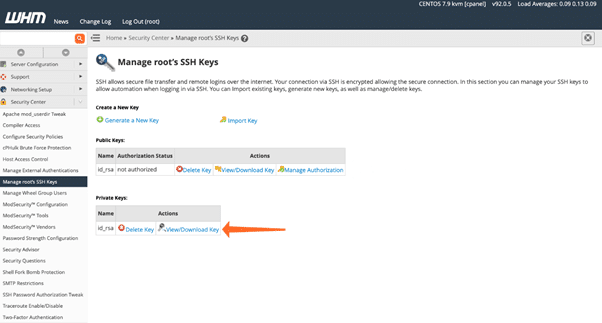
The upcoming step is differs depending on your operating system and SSH client. If anyone uses the built-in Microsoft windows 10 SSH or open SSH on macOS or Linux, you must create a file known as id_rsa.pub and then stick the private key data into it. If you have a key name, you can use it instead of the id_rsa filename.
To make your default private key.
On Windows, save this in the Usersuser1. ssh directory.
Linux and macOS, help you save it in the /home/user1/. ssh directory.
Replace User1 with your login name. Then try to connect your server over SSH as usual, utilize the authentication kay rather than your password.
If you do not want to make it your arrears private key, save this elsewhere and specify the key when logging in.
ssh -p 32356 -i my_public_key [email protected]As the things stand, the root user can log in with SSH keys or a password. If you would like to force users to authenticate with keys and want to prevent them from applying a password, try to enable the SSH code authorization tweak in the home security centre.
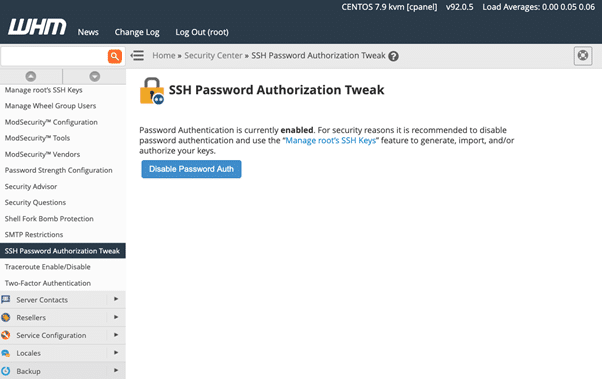
Fighting Brute force attacks with cPHulk
If you have locked down the SSH but still there are several other services bots might desire. The cpanel and the WHM include the cpHulk, a brute force protection tools that monitor the Cpanel, WHM, Mail, ssh ports. You can find the cPHulk in the WHM security centre. By default, if it is disabled, click on the switch and enable it and access the configuration interface.
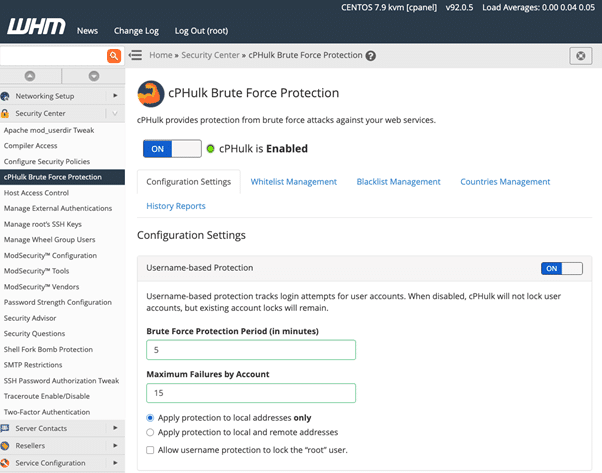
We have selected sensible defaults, but you can certainly tweak several settings to the user and IP brute-force monitoring:
Maximum failures determine the number of was not able authentication attempts before the user or IP is blocked.
Brute Force Protection Period determines how quickly the maximum malfunction rate is reached.
For example, in this image, IPs are blocked if they make a lot more than five failed login attempts in 15 a short time.
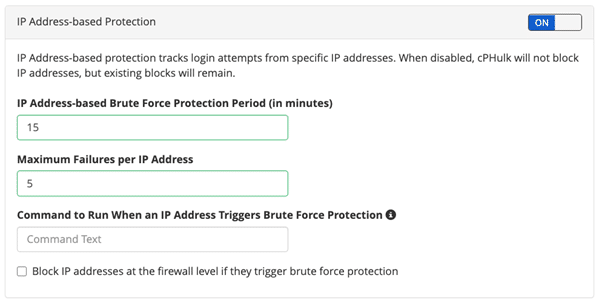
cPHulk also includes whitelisting for IP addresses and users that might never be blocked and blacklisting for those that will always be plugged. (Note that these terms are likely to switch in the future to make them more comprehensive)
Follow Linux Security Best Practices with cPanel Security Advisor
cPanel Security Advisor will scan the Linux servers and programs for misconfigurations that could cause security vulnerabilities. It generates warnings alongside recommendations with guidance to help administrators to secure his or her server.
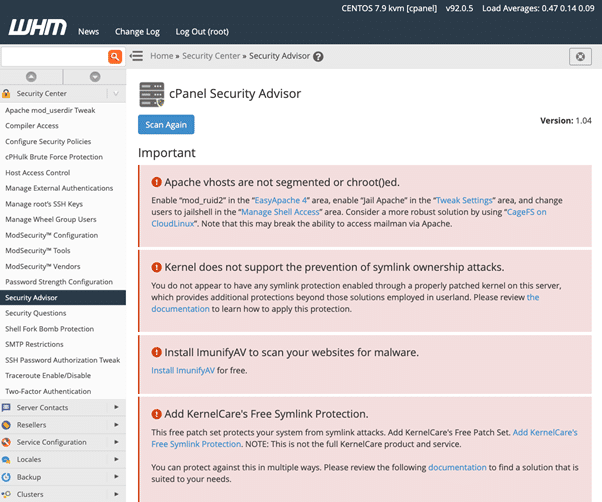
Linux Server Security with cPanel & WHM
There are a lot of security features that available in the Linux security features which will empower hosting providers and server administrators to protect data, limit the impact of malicious users and defeat brute-force and many other bad bot attackers.
Conclusion
In short, The Linux security enhancement with Cpanel & WHM help server administrators to build a secure hosting environment.

