A recent Apache HTTP server update has unintentionally caused widespread website outages, particularly affecting systems running NGINX as a reverse proxy in front of Apache—a common setup in hosting panels like Plesk for Linux. The sudden spike in 421 Misdirected Request error has led to confusion across the hosting and DevOps community, especially for users relying on SSL/TLS termination via Apache.
Let’s break down what caused the problem, who it’s affecting, and how you can fix it.
What Happened: Apache’s Security and the SNI Mismatch
- Apache Security Update Implemented : Aimed at mitigating recent CVE vulnerabilities, Apache introduced stricter SSL/TLS policies.
- New Requirement: SNI Enforcement : Apache now mandates that Server Name Indication (SNI) must be explicitly provided during SSL/TLS handshakes.
- Default NGINX Behavior Causes Conflict : By default, NGINX does not forward the server name via SNI when proxying HTTPS traffic to Apache.
- Result: Apache Rejects the Connection : Without a valid SNI, Apache returns a 421 Misdirected Request error, halting the request.
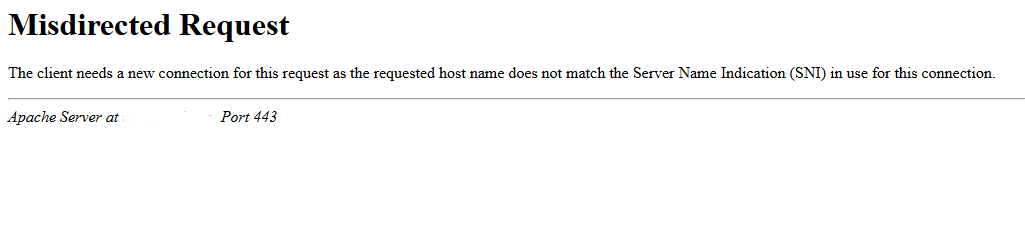
And in Apache logs (or Plesk logs), the error may appear as:
AH02032: Hostname (default host as no SNI was provided) and hostname www.example.com provided via HTTP have no compatible SSL setupWho Is Affected?
This issue spans multiple platforms and providers:
- Plesk for Linux users, especially versions 18.0.70 and 18.0.71
- Web hosts using NGINX → Apache reverse proxy chains
- Cloudflare users – some reports of disruptions in proxied setups
- Any stack that uses NGINX to proxy HTTPS to Apache without explicit SNI forwarding
The Immediate Fix: Enable SNI Forwarding in NGINX
To resolve the issue, you must explicitly configure NGINX to forward SNI headers to Apache. Here’s a quick fix for systems like Ubuntu 22+ and Plesk:
SSH into your server and Run the following command to configure NGINX:
This command will Add proxy_ssl_server_name, proxy_ssl_name and proxy_ssl_session_reuse directives in nginx configuration to make nginx pass the server name to Apache through TLS Server Name Indication (SNI) extension:
echo -e "proxy_ssl_server_name on;\nproxy_ssl_name \$host;\nproxy_ssl_session_reuse off;" > /etc/nginx/conf.d/fixssl.conf && systemctl restart nginxAlways back up your server configuration before applying changes.
This fix restores website functionality by ensuring the server name is passed during TLS handshakes—matching Apache’s new strict SNI enforcement.
Global Scope: CDN and Proxy Implications
This issue goes beyond control panels—it impacts the entire web ecosystem using layered proxy/CDN setups:
- Cloudflare and other CDNs may see similar errors if their backend servers (NGINX/Apache) are not aligned in SNI handling.
- Shared hosting platforms are experiencing mass outages post-update.
- Reports across forums and support channels indicate widespread confusion and downtime.
Lessons for DevOps & Hosting Providers
This incident is a powerful reminder of the need for proactive infrastructure awareness:
- Monitor changelogs and vendor advisories closely.
- Implement automated rollback and backup strategies.
- Stay aligned with server management team like us to fix this kind of problems immediately
Final Thoughts
The 421 Misdirected Request issue demonstrates how tightening security in core components like Apache can have far-reaching effects, especially when layered technologies like NGINX and CDNs are in play.
Action Checklist:
- Apply the NGINX fix for SNI forwarding
- Monitor updates from Plesk or your control panel vendor
- Avoid Apache downgrades unless absolutely necessary
- Stay informed on vendor responses and security advisories
Maintain resilient, secure, and well-communicated server environments—because in the DevOps world, uptime matters, but it’s only achievable through proactive and consistent server management.
Still facing the 421 Misdirected Request Error? Don’t let server issues slow you down. With our Server Management Services, we diagnose and resolve errors quickly, ensuring minimal downtime and peak performance.

